Greetings!
As you all know, well-managed and secure remote access is a key aspect of Microsoft solutions. As most of us have seen, working remotely has taken on new scale and urgency right now and people across Microsoft have published some great reminders/guidance to help:
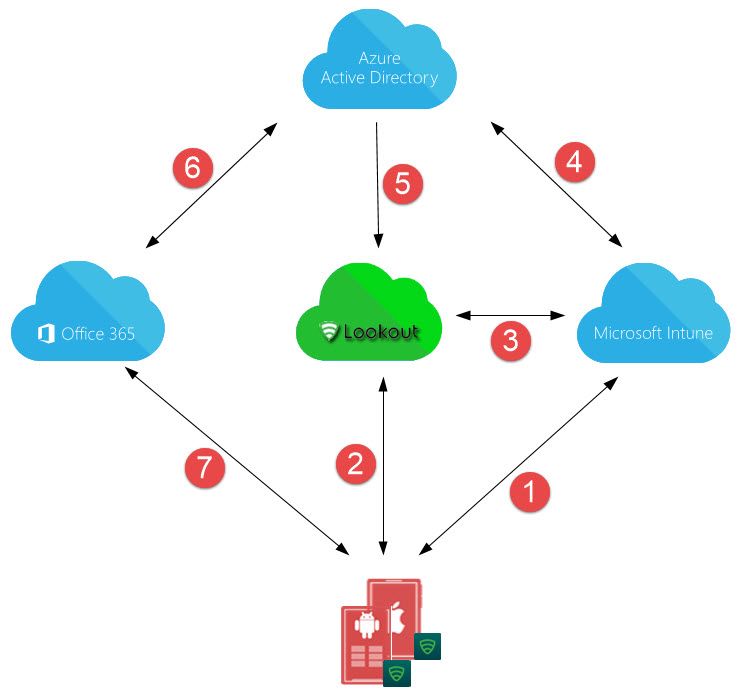
Intune + Microsoft 365 Education Get everything you need to set up, configure, and manage your Windows 10 devices with Intune, included in every Microsoft 365 Education device license. Intune + Microsoft 365 Education Get everything you need to set up, configure, and manage your Windows 10 devices with Intune, included in every Microsoft 365 Education device license. Now with Office 365 integration with Intune will provide more richer features and capabilities!! These MDM features are freely available for all office 365 customers. Microsoft is planning to release this integration by 1st quarter of 2015. Microsoft Intune, included with Enterprise Mobility + Security, lets you manage Office 365 mobile apps so you can maintain the rich, productive Office user experience while Intune helps keep your corporate data secure.
As a former IT Pro (and still one at heart), I know that during times of trouble, there is real value in having crisp, concise ‘just tell me what to do’ guidance. In this post, I’ll offer a ‘cut to the chase’ option for Intune that can help enable remote workers on BYO/unmanaged or 3rd party MDM-managed mobile devices with a minimum of impact to your current-state.
With any rapid-deploy change, there is heightened worry around the IT version of the Hippocratic Oath – ‘First, do no harm.’ This could be “Don’t blow up my end-user’s experience (nor my Helpdesk)” or, it could be, “Don’t drop my security posture to the floor.”
To that thought, I’m offering a “lighter hand” here – apply Intune MAM policy to Office Mobile Apps if/when they are used to access O365 content – but don’t block existing native app access, nor require device enrollment into Intune (think: personal device or existing 3rd party MDM).
- IMPORTANT: One of the goals of this post is to avoid impact to people already using the native apps on mobile devices to access O365. If you’re already blocking this, great – that is/was/continues to be our guidance. However, if you’re not there yet, this is a step towards that goal. Holistically, continue your work, driving towards a layered approach to security. This includes blocking legacy authentication, requiring managed apps, intelligent MFA, device-based trust, etc. The information offered here is a part of that ‘zero trust’ approach – but consider it just one piece of ‘low hanging fruit.’
Ok, let’s cut to the chase…
Scenario
- Enable remote workers to create/update/save/collaborate on corporate content in O365 (SPO/OD/EXO) from un-managed mobile devices (BYO mobile phones and/or tablets) while reducing risks to that data
- Limit download/save as to a local device
- Limit cut/copy/paste to ‘un-managed’ apps
- Limit printing
- Require a PIN or biometric to open the Office Mobile Apps
- Enable selective wipe of corporate data from IT (via the Intune Portal) or the end user (if/when they remove the corporate account from the Office apps) – but don’t affect anything else on the device
- Such as photos, personal email, files, etc.
Solution: Apply controls to Office Mobile Apps on mobile devices
- Here, when the user signs in to the Office Mobile Apps with corporate credentials, the App “phones home” to your Intune MAM Service “back-end” and checks for any MAM Policies. If the user is targeted for any, the apps pull down the Policy settings and apply them.
- At that point (almost immediately), the app will notify the user that it’s now under policy control and the app will close.
- Intune MAM docs:
- MAM Without Enrollment reference – HERE
- MAM reference – HERE
- MAM settings reference – HERE
Solution Steps
- As always, you can/should use Groups to target/scope your rollouts – this could be a new or existing on-prem AD group that syncs to AAD or a CloudA self-service, pay-as-you-go model of providing computing resources to an organization or to the general public.
Cloud Computing evolved from existing technologies such as a fast and reliable Internet, virtual operating environments including virtual machines and virtual storage and is provided...More...' target='_blank'>cloud-only AAD group- Add your pilot users to that group
- You can easily use Group-based Licensing to ensure your users in the group have a required Intune license <HERE>
- Intune is included in the “E3” suites – M365 E3 or EMS E3.
- From the Intune Portal, create an “App Protection Policy” (APP) – aka “Mobile App Management” or MAM Policy – with a Name and Description…
- Select your target apps

- Select your data protection settings for cut/copy/paste and data encryption, etc. (the “i” tool-tip can help explain the options, or refer to our docs, link above)
- Select your app access requirements (such as a PIN for the apps, how often to re-enter the PIN, allow biometric instead of a PIN, etc.):
- Define your conditional launch settings:
- Assign your policy to the Group you created in Step 1
- Note – you can also use an ‘exclude’ group to further control targeting
- Review and complete the wizard:
Results
Now, when licensedIntune users in the targeted group sign-in to the Office Mobile Apps with their corporate creds, the MAM policy settings will apply to those apps and the corporate data within them.
For example, they’ll be prompted to setup an application-level PIN and will be blocked from cut/copy/paste of corporate data out of the policy-managed apps.
Office 365 Download
- “What does it look like for my end-users?”
- App PIN – This PIN can (should?) be different than the device PIN (however, we don’t have a control to force that – educate your end-users on that point)
- This can keep the kiddos out if they know your iPad PIN and use it to play Tetris, Space Invaders or even Pong (age-reference :smiling_face_with_smiling_eyes:)
- App PIN – This PIN can (should?) be different than the device PIN (however, we don’t have a control to force that – educate your end-users on that point)
- Prevent copy of ‘managed corporate data’ into local un-managed applications
- Prevent Save as to un-managed locations (Files App or ‘On My iPad” is blocked; SharePoint Online and OneDrive for Business is managed/allowed):
You can now ‘encourage’ your users to install/use the Office Mobile Apps when accessing O365 and know that the corporate data will be well-protected.
Remember, in this specific case, we’re trying to ‘do no harm,’ so we “encourage” vs “require” …
- Of course, recall from the beginning of the post, you could use (and should consider) Azure AD Conditional Access, and other controls for layers of security for more stringent access control:
- Block (or limit) “the un-managed” – personal devices, native mail clients/apps that don’t support MAM Policies
- Require “the managed” – MDM devices, Office Mobile Apps/other apps that support MAM Policies
Notes/FAQs
Office 365 Mdm Vs Intune
- As mentioned, this solution does NOT require Intune-enrolled devices; they can be un-managed or even managed by a 3rd party MDM.
- It does require an Intune license for the users in your target group, though.
- There are additional/other access control capabilities in M365, such as AAD Conditional Access, Microsoft Cloud App Security (MCAS) and others, but this specific configuration is super quick and easy – and pretty low-risk on the ‘do no harm’ scale.
- “What if users already have Outlook Mobile on their devices and their personal email account defined?”
- No problem – we leave the personal email accounts alone both during policy application and if/when the app is selectively wiped (either by IT or by the end-user removing the corporate account from the app)
- iOS users may be prompted to install the Microsoft Authenticator app on a BYO device
- For instance, if you have existing app-based Conditional Access Policies setup in Azure AD that require device registration in AAD, iOS uses the MS Authenticator App to perform the device registration in AAD
- Android users will be required to install the Microsoft Intune Company Portal app (if they don’t have it already installed)
- They don’t need to enroll the device into Intune, though, only install the app – ensure you educate your users/helpdesk on this point.
- While this model of using Intune MAM is generally pretty ‘low impact’ (no blocking access), you should always do your due diligence and test your specific scenarios, in your specific environment, with your current configs and device types. Be sure to pilot the roll-out and control the ‘pace of change’ – even if it’s faster than normal.
- These policies are ‘scoped’ to groups – you can/should start with a group of a few users to validate the results/behavior.
- As you gain comfort with the results, expand the group members at the speed of your org’s choosing/comfort:
- 5-10 users > 20-100 users > 250-1000 users … ?
Office 365 Intune Cost
If you need/want more assistance, you have several options:
- Microsoft Fast Track – anyone with 150+ licenses can use the Fast Track Center to request assistance/guidance. <HERE>
- Microsoft Premier Services/Microsoft Consulting Services/Unified Support – anyone with a Premier or Unified Support contract can reach out for help – contact your Technical Account Manager (TAM) or <HERE>
- Microsoft Partners – if you are working with a Microsoft Partner, hit them up – They’re always willing to help.
- Our own docs – <HERE>
Best of luck as we all work through these “highly-uncertain” of uncertain times!
Microsoft Office 365 Intune
Hilde
